MINNEAPOLIS - Twin Cities computer security expert Mark Lanterman says all Minnesotans should be alarmed that a hacker was able to break into 23 state databases.
“This is a serious deal,” Lanterman said.
Using the name "Vigilance," the hacker posted online some of the information he found – including names, addresses, phone numbers, email addresses and confidential passwords.
In an interview through Twitter messages, the hacker said, "They include state employees, contractors and private citizens."
“I think he did it to prove a point, but it definitely could have been a lot worse and I think we should be thankful that he stopped when he did,” Lanterman said.
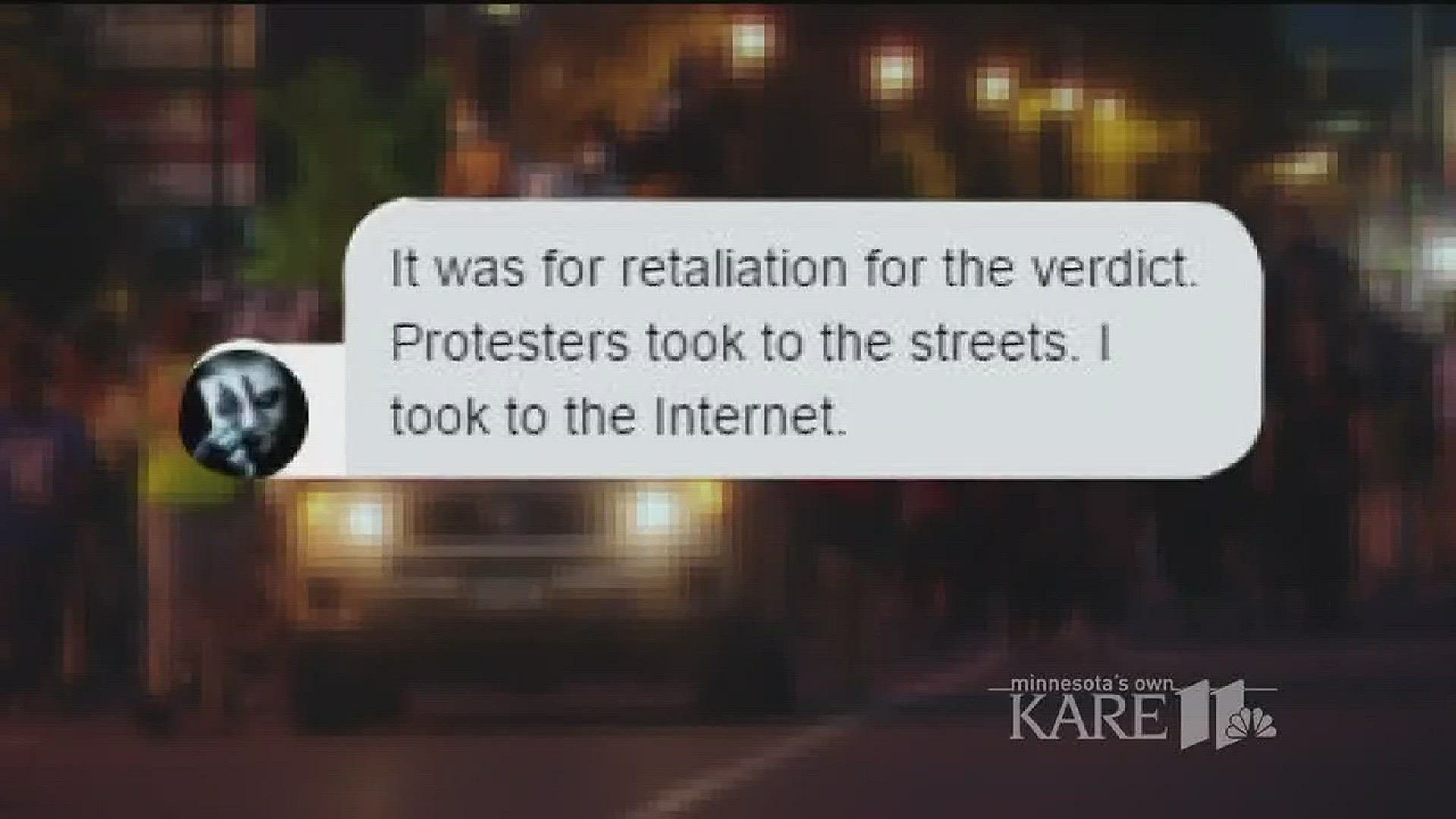
The reason he did it, the hacker said, was the not-guilty verdict in the Officer Jeronimo Yanez trial.
"It was retaliation for the verdict," he told KARE 11. "Protesters took to the streets. I took to the Internet."
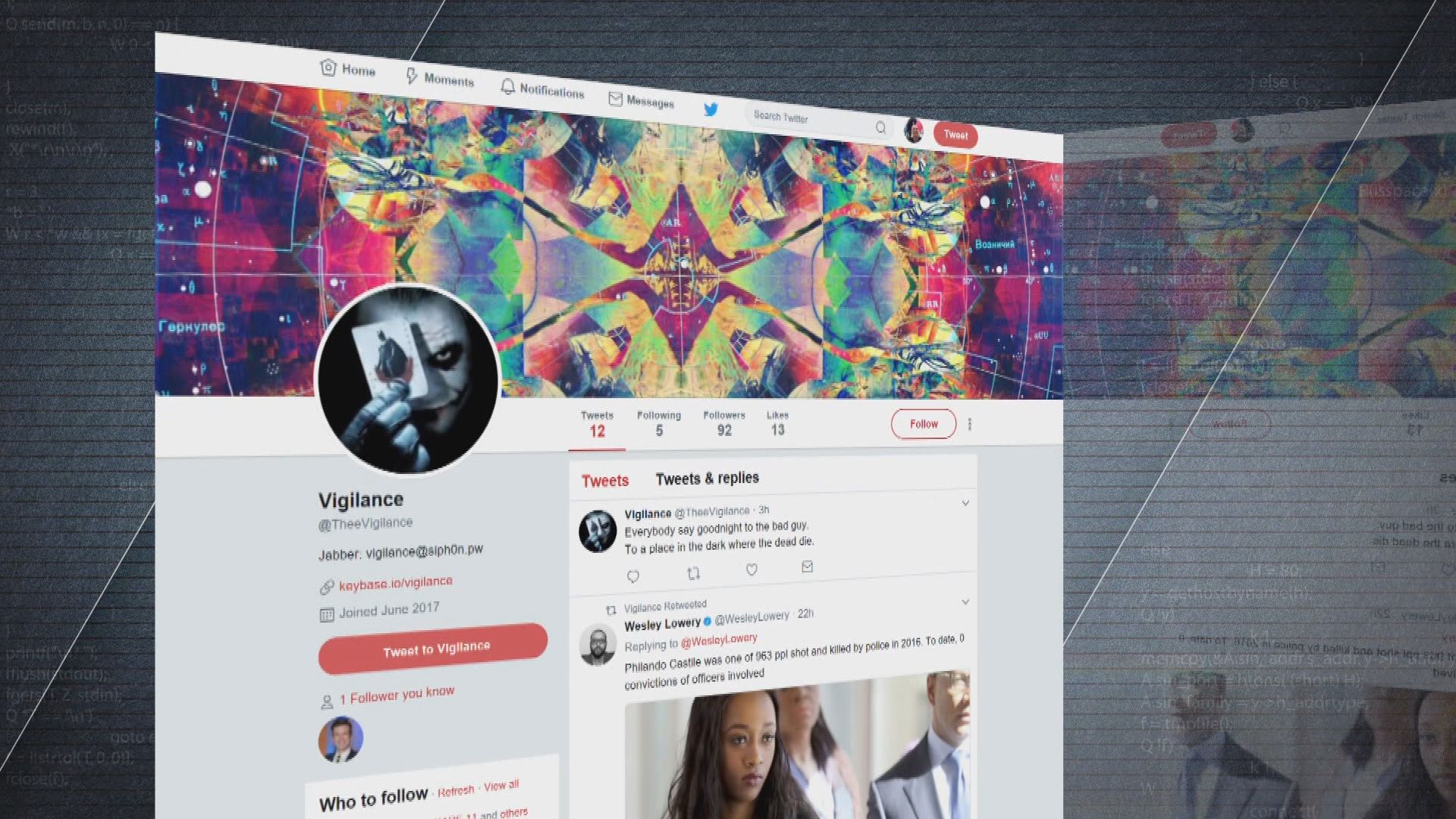
Lanterman says hackers like this are known as "hacktivists"
“If he wanted to commit identity theft, he would have done it a different way. I think here he wanted to disrupt the state, prove that he could do it, but I think he used the breach to gain attention for his viewpoint,” Lanterman said.
Lanterman said the state has ignored him in the past when he's raised concerns about security vulnerabilities – and says we should feel lucky the hacker didn't have worse intentions.
Late Wednesday, Minnesota IT Services sent the following statement:
“As previously reported, Minnesota IT Services has determined that a server housing several legacy state technology applications was accessed without authorization by an external actor. This hack impacted a very small portion of the State of Minnesota’s technology infrastructure, primarily affecting legacy computer systems that are no longer in use.
“This event did not impact any major business systems that support state government operations. In this incident, the hacker exploited a weakness in the state system that resulted in the hacker’s ability to access the data inside. The data that was posted online appears to be consistent with what our investigation has found, including email addresses and encrypted passwords of subscribers to old government newsletters (for example, energy permitting program updates).
“After learning about the potential breach, Minnesota IT Services’ Computer Forensic Team immediately took steps to assess the validity of the claim and concluded that the server had in fact been compromised. Minnesota IT Services worked quickly to remedy the vulnerabilities and strengthen security controls. We anticipate that we will be turning over the information resulting from our investigation to the FBI today.
“Minnesota IT Services will be reaching out directly to those who are affected, primarily subscribers to state geographic information and energy program newsletters. As always, we recommend that people use unique passwords for every account they use. Out of caution, our recommendation to those who are affected is that they consider the passwords compromised and reset them anywhere the same password might have been used.
“While Minnesota’s systems are probed for vulnerabilities more than 3 million times each day, our state has fortunately not yet experienced a major attack exposing Minnesotan’s private data. However, Minnesota has experienced incidents that have exposed state systems and data to significant risk. Nearly every government function that Minnesotans depend on is reliant on technology, but many of the systems we use today run on outdated, unsupported technology that makes them a prime target for attack. Recognizing the growing threat, Governor Dayton proposed a significant investment in cybersecurity during the last legislative session to modernize state systems and strengthen cyber defenses to better protect Minnesotans. Events such as these underscore the urgency of this increased investment.”